-
Organizational Measures
To ensure that we can respond swiftly and comprehensively to every security risk, we have an organization called “Cybersecurity Office (CyberAgent CSIRT)” which consists of representatives from each business and department such as information system, law affairs, public relations, internal audit, and security promotion, including two executive officers, and we have a group-wide information security management system in place. We also have a special security organization called “Security Promotion Group” in place, which consists of experienced security professionals, in order to prevent information security incidents that are changing and becoming more complex every day and ensure that we can respond smoothly to them.
Cybersecurity Office (CyberAgent CSIRT) is a member of the Nippon CSIRT Association and the Forum of Incident Response and Security Teams (FIRST) and realizes appropriate incident responses by working together with external organizations.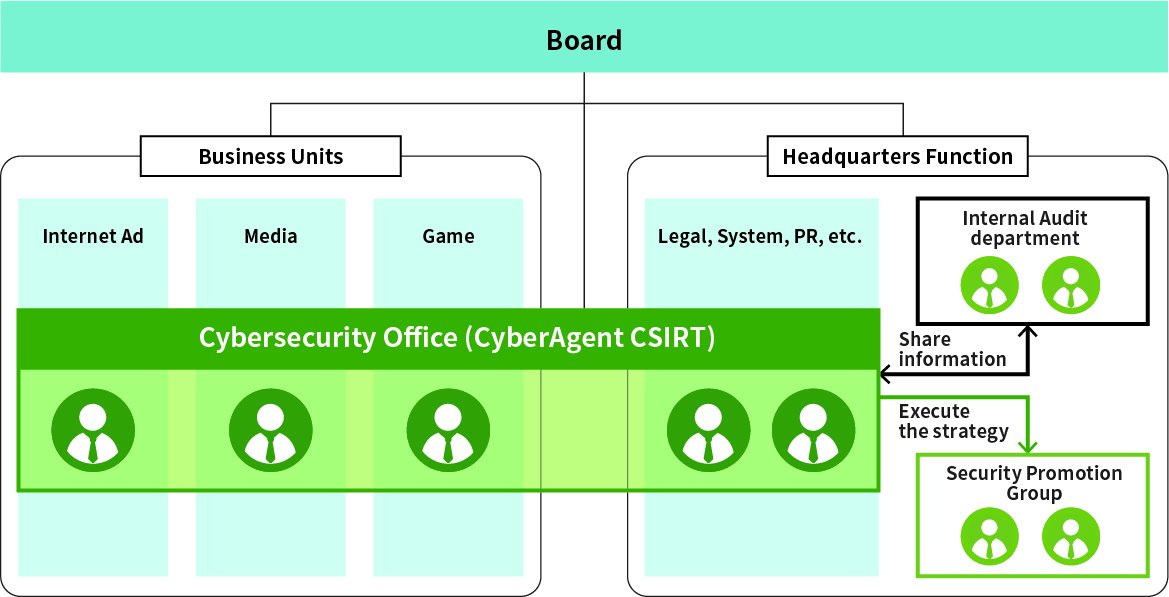
Information security system chart

Security officers from each department gather in the Cybersecurity Office (CyberAgent CSIRT)
-
Human Measures
To raise awareness of information security among all employees, we collect and provide information and enlighten them by, for example, launching a special information website publishing with content using manga to explain the importance of security in an easy-to-understand manner from various perspectives.
We also provide security education for employees using an e-learning system. We encourage employees to acquire the knowledge necessary for their professions by providing content tailored to the duties of each employee, such as content for service development engineers or service planning professionals, in addition to content that helps understand the information security basics and the Personal Information Protection Act.

-

Technical Measures
Internal Systems
We centrally manage the employee accounts with a user management system connected to the HR database and limit the use of internal systems and access to the internal network by unauthorized users.
We have malware protection measures in place, ranging from general virus protection to advanced malware protection measures depending on the professions and the risk level of the business and operation. We always monitor the system to detect and respond to cyberattacks from external sources.Service Development
Security Promotion Group, a special system security organization, has developed security guidelines on service development. We have a support system for secure service development in place, which is ready to respond to consultation from divisions in the service planning and design phases.
We also have a system to centrally manage the accounts for the development environment and manage users and rights for each project properly. We perform vulnerability diagnosis before releasing new services to solve problems that may lead to security incidents. We also perform vulnerability diagnosis for the main services in operation once a year. -

Physical Measures
Office
Access to offices is controlled with a security card. We have enhanced information security measures in place to, for example, control access to rooms and install security cameras depending on the security level of information handled.Data Center
The data centers we rent are equipped with full-fledged disaster resilience measures to ensure that personal information and system infrastructure are managed securely. The data center is divided into areas from levels 1 to 7 depending on the importance level and various measures are in place to prevent natural disasters and avoid human risks, including controlling access to the building and rooms with security staff and card authentication, checking devices brought in and taken out, and monitoring with multi-element authentication and security cameras.
CyberAgent acts to reduce various risks involving information security in four areas, Organization, People, Technology, and Office. To continue business growth, we protect our users by enhancing our information security measures and providing reliable, safe, and secure services.